Introduction
A phishing attack is one of the most common tricks hackers use to steal passwords, bank details, or personal information. In this guide, we take an inside look at how hackers trick you with fake emails and websites, highlight the phishing email red flags you should never ignore, and show you how to protect yourself from phishing using stronger tools like passkeys, MFA, and smart online habits. According to Microsoft Security, phishing is one of the most common online threats, used to steal passwords and sensitive data.”
Phishing emails can mimic the appearance of official company emails or even those from friends or family. The objective is straightforward: trick the victim into giving over sensitive information by making them feel rushed or trusted, such as by forcing them to open a file or click on a link. Once that occurs, malicious actors can evade security measures, get personal information, or even infect complete networks.
Identifying warning signs and using countermeasures can help you and your company stay safe during a phishing attempt. We’ll take you through each stage of the campaign, from the initial email to the attacker’s final objective.

What you’ll learn in this overview
- What happens in a phishing attack, from the first lure to taking over an account
- What to check for in emails, links, and websites that can be fake
- How to protect yourself at every level
- What to do next if you clicked
Step 1: How a Phishing Attack Begins
Attackers utilize a believable tale, including a fake invoice, a password reset, a delivery from a courier, a letter from HR, or a bank alert, as a “pretext.” They utilize names, logos, and writing styles from public sources to make it look legitimate.
Signs of trouble
- Unclear context: “There is a problem with your account.”
- Spontaneous “urgent” demands (pay now, reset now, verify now)
- The sender’s email address comes from a personal or unusual domain.
Defend
- When someone asks for something right away, be skeptical.
- Always Verify (Use the official phone number, not the email link.)
- Teach your staff that haste is a common social engineering tactic.
- “Phishing starts with a believable story that makes you feel like you have to act right away.”
Step 2: Spotting Phishing Email Red Flags
The email features familiar branding and language. The display name may appear appropriate, but the From address or Reply-To address is usually different. Buttons can hide links.
Warning signs
- The display name does not match the sender’s domain.
- Small mistakes in domains, like paypaI[.]com using a capital “I”
- Banner from an outside sender on what looks like an inside email
- Bad grammar or strange, generic greetings
Guard
- Hover over links to see where they really go.
- Consider using a password manager, as it will not autofill your password on fraudulent sites.
- Small differences in the sender’s email address and the links can often indicate phishing attempts.”
Step 3: How Hackers Trick You into Clicking
Links take you to phony login pages or viruses. Attachments typically include macros or links built in.
Warning signs
- Shortened links that hide where they go
- HTML files that open a bogus login page
- Office documents that say “Enable Content/Macros”
Protect
- Use a different device, profile, or browser sandbox to open URLs that look suspicious.
- Don’t let macros run; set a policy that blocks them for files from the internet.
- Use Safe Links, URL rewriting, and attachment sandboxing to keep your files safe.
- Caption: “Hovering over the link usually shows the real destination.”
Step 4: The Fake Page: Collecting Credentials
The landing page looks like the actual brand. It could even redirect you to the legitimate service after obtaining your password, leaving you unaware of the theft
Warning signs
- The domain name doesn’t quite reflect the genuine service.
- The login page came via a subpath on a site that had nothing to do with it.
Defend
- Look at the whole domain, not just the design of the page.
- If the domain doesn’t match, password managers won’t fill in the form automatically.
- “Design can be copied; the domain is the truth.”
Step 5: The Bypass: How to Beat MFA
Attackers could utilize push fatigue (bombarding you with MFA prompts), reverse proxies to steal session cookies, or ask you to input a one-time code on their site.
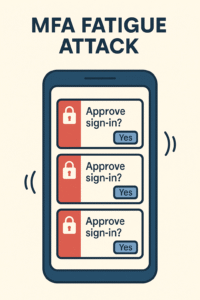
Conventional phishing tricks you into entering your username, password, and MFA code by using a fake login page. More sophisticated is proxy phishing: In this technique, the attacker installs a reverse proxy server between you and the actual website; when you log in, everything you write is immediately forwarded to the actual website by the proxy server. This implies that they steal not just your password but also your session cookie or MFA token. As a result, the attacker circumvents most barriers and accesses your account as if they were you.
Warning signs
- MFA prompts that come up at strange times
- Several MFA push requests could be a sign of an attack.”
- A website that asks for your password and your MFA code on the same page that you don’t know
Protect
- Use passkeys to protect yourself from proxy phishing.
- If you continue receiving MFA requests, please decline them and inform IT.
- “If you keep getting MFA requests, it could mean that someone knows your password.”
Step 6: After the Hook: Access and Staying in Power
Once inside, the attackers search through financial tools, cloud storage, and emails. They may make rules for their mailboxes to conceal alarms, make passwords for apps, or add rules for forwarding.
Warning signs
- New “Rules” alerts in email settings that you haven’t read yet
- Devices or tokens that aren’t recognized on account security pages
- OAuth apps that you don’t know about but have a lot of access
Protect
- Turn on anomaly detection and alerts in your email.
- Change passwords and end all current sessions if there is a breach.
- Please review the guidelines for mail, forwarding, app passwords, and OAuth permissions.
OAuth, which stands for “Open Authorization,” is a way to enable apps to use your account without giving them your password. For example, you open a new app and click “Sign in with Google.” Google doesn’t want you to share your password with that app. Instead, it asks, “Do you want this app to be able to see your profile, email, and drive files?” The app gets a token, which is like a digital key, that lets it see what you let it see. The app can keep using that access without asking you again once you provide it to them.
When you say yes, you’re stating,
- “This app can see my email.”
- “This app can access my Google Drive files.”
- “This app can send emails for me.”
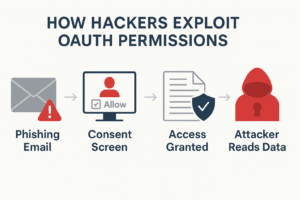
Therefore, before you click “Allow,” read the permissions carefully. If an app asks for too much, like full access to your email for a simple calendar application, say no.
- Check your account occasionally to see what apps are connected:
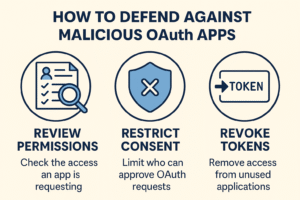
When you give someone OAuth permissions, it’s like giving them a spare key to your house.
Step 7: The goal is to steal data or cash out
Common steps include fake invoices, gift card fraud, payroll adjustments, or selling access.
Warning signs
- Changes to vendor bank details communicated by email
- Sudden offer of gift cards or demand for payments that need to be made right away
- Files downloaded in bulk from cloud drives
Protect
- Use methods to check payments, such as dual approval and call-backs.
- Set online withdrawal limits behind specific approvals
- Log and provide alerts for large downloads and strange API activity.
- “Never approve changes to your finances via email alone.”
If you clicked, you need to take action right away
- If you think malware is on your computer, disconnect from the network.
- Change your password (from a device that is clean)
- Cancel sessions and tokens; log out of all devices
- Please review the settings for your mail and forwarding, and remove any items you are not familiar with.
- Enable or enhance MFA (preferably passkeys or security keys)
- Send the original email as an .eml file to your IT/SOC.
- Monitor your bank, payroll, and cloud accounts for any unusual activity.
Conclusion
Phishing is still one of the best methods for cybercriminals since it takes advantage of people’s trust and mistakes instead of technological problems. Attackers are always coming up with new ways to trick people, from fake emails and malicious links to more advanced methods like MFA fatigue and mailbox rule manipulation. But people and businesses can turn things around by being aware, staying alert, and using better security like passkeys and MFA that can’t be fooled by phishing. It’s not about being afraid of cybersecurity; it’s about being ready. We can make sure that a simple click never turns into an expensive breach by learning to detect the warning signs and act fast.
“The CISA recommends using secure email gateways, browsing protections, and hardened endpoints to stop phishing emails before they reach users.”
For detailed information about cyber attacks, please click the link below:



